MySQL is a strong, however difficult database administration system – as fashionable as this RDBMS may be, there are nonetheless questions surrounding it – one of many essential ones being associated to safety. On this weblog, we’ll inform you all the things it’s good to know to construct a safe basis in your knowledge utilizing MySQL.
As builders, we already understand how vital it’s to make sure that the techniques we construct carry out at the perfect of their capacity. Nevertheless, an typically uncared for aspect of software and particularly database improvement is safety. How can we construct databases which can be resilient to the assaults that concentrate on our infrastructure? We all know you‘re already acquainted with primary assault vectors like SQL injection, however within the database world, there‘s a lot extra to that. Allow us to stroll you thru all the things it’s good to know.
Architecting for Safety – the Fundamentals
Our databases gained’t be protected if our functions are flawed, so to begin with, familiarizing your self with 10 of probably the most prevalent threats for net functions – the so-called OWASP Top 10 – is an effective start line.
The OWASP High 10 is a frequent start line for builders that need to safe their software program, and it‘s a very good one at that – the OWASP High 10 gives ten of probably the most harmful safety flaws focusing on our software program and databases, and it‘s often known as the industry-standard follow for securing net functions. Some builders additionally familiarize themselves with GDPR, ISO 27001, and HIPAA in the event that they‘re working for a corporation that requires these, however for many, OWASP gives a extremely good start line.
Architecting for Safety – Assaults and Information
Earlier than we shield our databases, we should make sure that our functions are protected and we will accomplish that if we make use of safe coding rules and observe the recommendation contained within the OWASP High 10. Doing so is essential as a result of the assaults outlined by OWASP goal not solely functions however databases as nicely. Right here’s why all the things is so interconnected:
-
One of many major functions of a knowledge breach is to steal knowledge belonging to an organization, then promote it to different attackers for revenue. As soon as knowledge is bought, it‘s often utilized in credential-stuffing assaults to focus on different techniques of the identical sort or to mount identification theft assaults in the direction of individuals who have reused their passwords.
-
The extra entries a database has, the extra fascinating it’s to an attacker – a database with 300,000,000 rows will definitely yield extra „income“ when it‘s bought in comparison with its counterpart with 15,000 information – identification theft assaults are profitable, in spite of everything.
-
The worth of a database can be depending on the information courses in it – a database containing plain textual content passwords and SSNs would yield extra profit for the attacker than merely stealing usernames and hashed passwords (hashed passwords typically require substantial work to revert them again to a plaintext format.)
You get the purpose – life after a knowledge breach isn‘t precisely the sweetest one. There are some excellent news, although – most assaults threatening net functions will be simply fended off by following primary safety recommendation: make sure that your software just isn’t passing person enter straight right into a database with out verification, cleanse it the place you make person enter seen to the person to guard your net software from Cross-Site Scripting, use PDO when interacting together with your databases to fend off SQL injection assaults, and think about using a CDN just like the one offered by CloudFlare to guard your net functions from DDoS assaults.
All that may be a good start line – securing database administration techniques, nevertheless, is a distinct beast altogether. Learn on to grasp why.
Architecting for Safety – Securing MySQL
So far as MySQL safety is anxious, there are a number of issues we should always consider. The issues that we should always familiarize ourselves with embrace, however should not restricted to:
-
The safety of person accounts, password safety, and entry management.
-
The “depth” of privileges which can be assigned to a particular person.
-
Account locking, reserved accounts, and roles.
-
Safety plugins.
-
Backups.
We’ll now begin from the highest and transfer in the direction of the underside.
Consumer Safety & Entry Management
Maybe some of the apparent – and most vital – issues to safe are the person accounts since more often than not when customers set up MySQL they proceed with queries that look one thing just like these outlined under:
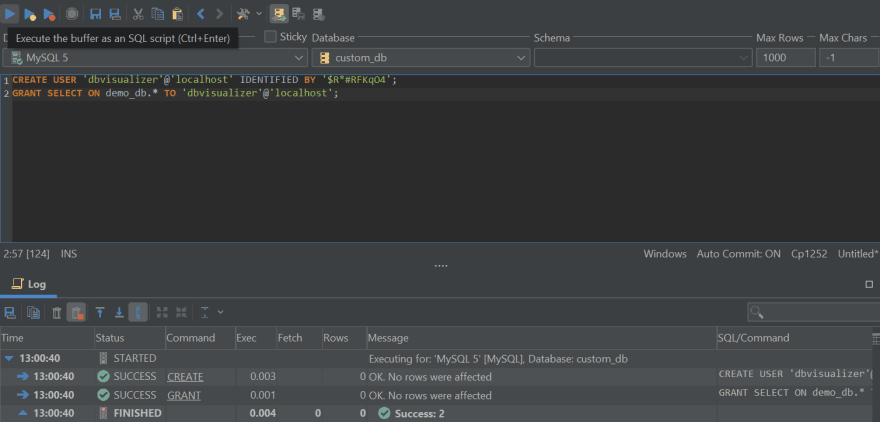
These two queries are a very good start line – one in every of them creates a person, and the opposite grants the person all privileges on a particular database. Select a powerful password, subject a FLUSH PRIVILEGES assertion to avoid wasting your modifications, and you’ll be in your means.
Upon getting taken care of “primary person requirements” so to talk, your person safety journey shouldn’t finish right here – regulate the next facets as nicely:
-
Make sure that the privileges which were assigned are completely vital to perform the duties of the particular person utilizing the account – keep away from granting all privileges if the person is simply going to run
SELECTqueries. All the time contemplate the angle of an attacker – if the privileges are restricted, so are his choices. -
All the time consider the capabilities of reserved accounts – these embrace the “root” person, the “mysql.sys” person, and the “mysql.session” person. These full the next functions:
-
The ‘root’@’localhost’ person is a superuser having all privileges throughout all MySQL databases. Take into account renaming the account to strengthen the safety on that entrance – a question like so will do:
RENAME USER ‘root’@’localhost’ TO ‘username’@’localhost’;
-
The ‘mysql.sys’@’localhost’ person is used to work with numerous procedures and capabilities associated to the MySQL infrastructure.
-
Lastly, the ‘mysql.session’@’localhost’ person shouldn’t a thriller as nicely – it’s utilized by plugins to entry MySQL.
-
It is usually very useful to understand that MySQL comes with highly effective password administration options, which might help you on a number of fronts too (we’ve offered some examples under):
-
MySQL might help you if you wish to expire a password of a particular person – doing so will be useful as a safety precaution or when following safety pointers outlined by the safety staff at your organization – see instance #1.
-
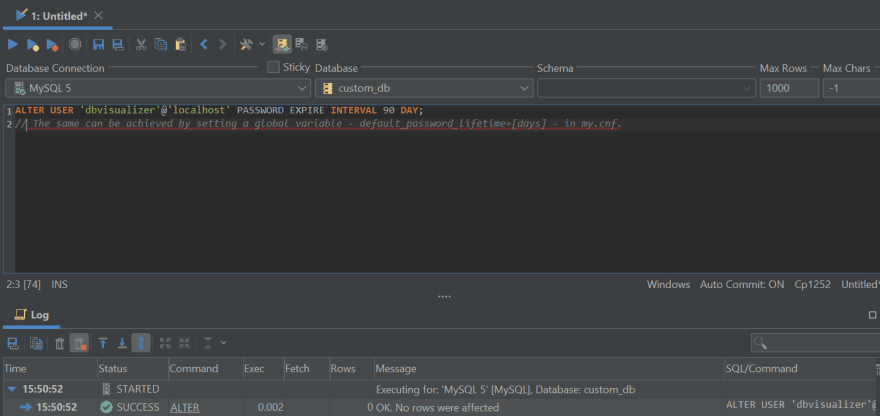
If vital, passwords will be set to run out after a sure time frame has handed – see instance #2.
-
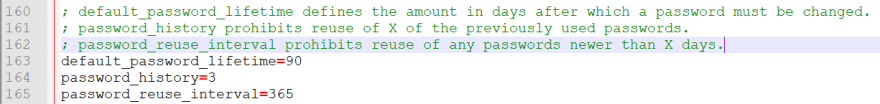
There are some choices that may be set within the MySQL configuration file (my.cnf or my.ini, relying on the working system that’s in use) that may make sure that passwords are reset after a specified time frame or passwords should not re-used earlier than a specified period of time passes – see instance #3.
-
It is usually useful to know that MySQL can generate random passwords (this one might be most helpful to those that are utilizing password managers to avoid wasting their credentials in – you don’t at all times have to make use of the password supervisor to generate a recent password for an account) – see instance #4 for the way MySQL might help. Needless to say you additionally should be operating MySQL 8 or above.
-
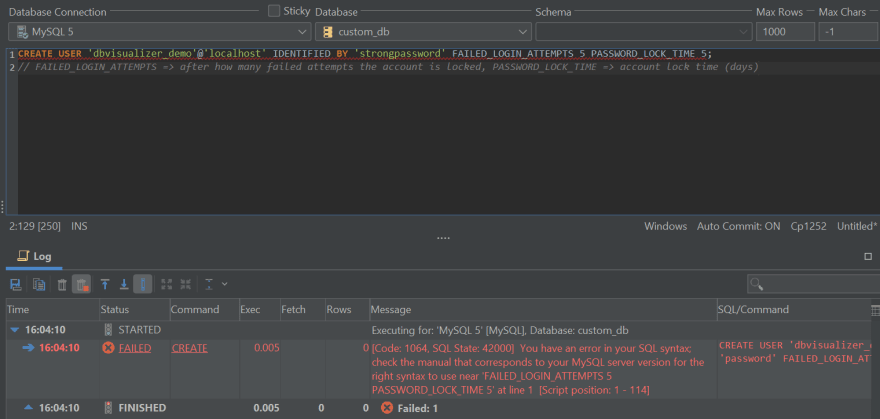
If you end up utilizing MySQL 8 or above (MySQL 8.0.19 or above to be particular), additionally understand that you can too quickly lock accounts after a specified quantity of login failures – this function can be utilized to forestall bruteforce assaults focused on the database – see instance #5.
-
Lastly, if you end up utilizing MySQL 8 or above, additionally hold a watch out for roles and account classes. Roles are primarily collections of privileges, and account classes distinguish system customers from common customers for higher management on the safety entrance:
-
Create a job by operating the
CREATE ROLEquestion like so:
CREATE ROLE ‘demo_role’;
Then, assign a privilege to a job:
GRANT INSERT, UPDATE, DELETE ON demo_db.* TO ‘demo_role’;
And at last, assign a job to a person by following the question under (substitute dbvisualizer with the identify of your person):
GRANT ‘demo_role’ TO ‘dbvisualizer’@’localhost
Needless to say MySQL 8 launched “system customers” to its infrastructure: assign a SYSTEM_USER privilege to a person to make it a system person – any customers with out such a privilege might be thought of to be common customers. The SYSTEM_USER privilege is required to handle person accounts (create customers and grant privileges to them) that means that common customers gained’t have the flexibility to run the CREATE USER and GRANT queries. All system customers even have the flexibility to kill classes and queries inside them and do a pair extra fascinating issues – to view the entire capabilities of a system person, refer to the MySQL documentation.


Safety Plugins
So far as safety plugins are involved, they fall into a number of of the next classes:
Firewall and audit plugins:
- Maybe some of the recognized such plugins within the MySQL house is the MySQL firewall – a firewall is ready to shield knowledge within the database from unauthorized exercise by blocking SQL injection assaults and detecting different intrusion strategies. Nevertheless, the firewall is an enterprise addition that means that the customers who elect to make use of this plugin can count on to pay a hefty worth (customers have to contact MySQL and ask for the firewall in an effort to purchase the product.)
Safe authentication and password plugins:
- Such plugins safe the authentication mechanism of MySQL. They might help customers select safe passwords – all it’s good to do is to incorporate the next line inside our my.cnf file and restart MySQL:
plugin-load-add=validate_password.so
As soon as that’s performed, you’d then have to set a password energy coverage by using the validate_password_policy variable. The password coverage you select could have a direct influence on the size of passwords that can be utilized – extra details about password insurance policies will be discovered here:
validate_password_policy=[LOW|MEDIUM|STRONG]
Connection-control plugins can provide safety from brute-force assaults: they can be utilized to extend the delay in MySQL responses if the connection makes an attempt exceed a specified quantity – implement the plugin by together with this line into your my.cnf file, then head over to the docs to finish setup:
plugin-load-add=connection_control.so
Finishing every of the steps coated above will value you a while, nevertheless, every of them rewards your database in their very own means – learn the documentation surrounding these safety measures if you happen to’re not too certain what they do, and solely implement these measures you totally perceive.
The steps above ought to assist you safe your MySQL infrastructure and put it on the safety freeway – make certain to again up your knowledge often and be at liberty to cease studying right here. After finishing the steps outlined above, the safety stage of your database infrastructure needs to be excessive sufficient to show intruders away. Nevertheless, true safety fanatics may need to proceed studying since now we’re going to leap into the waters of backup safety.
Securing Backups
Securing backups isn’t something revolutionary – on that entrance, we simply want to verify backups are saved securely, or in different phrases, in an encrypted style.
To encrypt backups, first take and check them, then if you end up utilizing Linux, use the next command:
$ openssl enc -aes-256-cbc -salt -in backup.tar.gz -out backup.tar.gz.encrypted -k password
the place:
To decrypt the backup, use the next command:
$ openssl aes-256-cbc -d -in backup.tar.gz.encrypted -out backup.tar.gz -k password
All the identical right here, simply be aware the “-d” a part of the command: it specifies that the password needs to be decrypted slightly than encrypted. First specify a path to the encrypted backup, then specify the identify of the decrypted backup file as an output (after the -out a part of the command.)
That’s maybe the best method to take care of safety concerning backups – nevertheless, if you happen to don’t need to encrypt your backups and you’d nonetheless desire to backup within the conventional style, make certain to specify your person and password beneath mysqldump in my.cnf (see instance under), then again up your knowledge as regular.

Doing so will allow you to run the mysqldump command with out offering a username and a password – that’s a very good safety follow since usernames and passwords will be noticed by trying on the final issued instructions through the terminal – nevertheless, when you’ve specified the username and password in my.cnf, you’ll be able to run mysqldump with out offering a username nor the password like so:
$ mysqldump database_name table_name > backup.sql
For all out there choices related to mysqldump, please discuss with the docs of MySQL.
Abstract
Securing the structure of MySQL isn’t the best factor to do – nevertheless, apart from defending our functions from distinguished threats like those outlined in OWASP Top 10, it’s an absolute necessity.
After you’ve familiarized your self with the strategies of safety, contemplate using the ability of data breach search engines to be informed once your account is in danger of identity theft, and you need to be good to go!
We hope you’ve loved studying this text – come again to the blog of DbVisualizer to study extra about databases and their interplay with functions after you’ve secured your infrastructure, and till subsequent time.
DbVisualizer is the highest rated MySQL client., download DbVisualizer for free and discover out what it has to supply!
Concerning the creator
Lukas Vileikis is an moral hacker and a frequent convention speaker. He runs one of many greatest & quickest knowledge breach search engines like google on this planet – BreachDirectory.com, often speaks at conferences and blogs in a number of locations together with his weblog over at lukasvileikis.com.
