Vulnerabilities produce huge reputational and monetary dangers. That is why many corporations are fascinated by safety and need to construct a safe improvement life cycle (SSDLC). So, at the moment we will talk about SAST — one of many SSDLC elements.
SAST (static software safety testing) is used to seek for safety defects in software supply code. SAST examines the code for a lot of potential vulnerabilities — potential SQL injections, XSS, SSRF, knowledge encryption points, and so forth. These vulnerabilities are included in OWASP Top 10, CWE Top 25 and different lists.
Earlier than we talk about why to combine SAST in a DevSecOps pipeline, let me draw your consideration to a few information.
The variety of vulnerabilities is rising. The price of fixing them is rising too
Reality #1: the variety of vulnerabilities is rising yearly
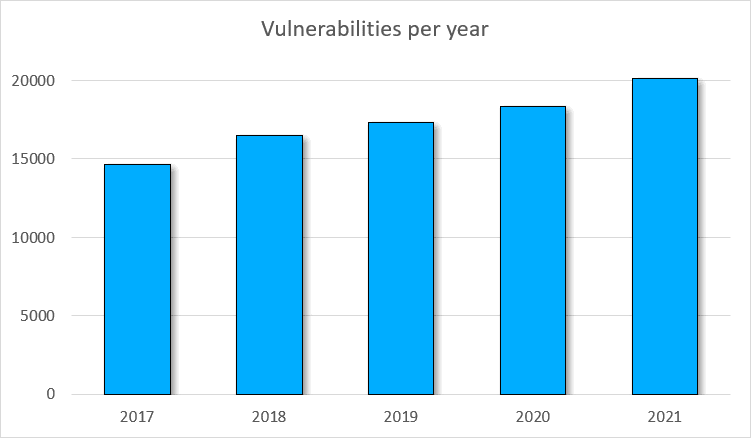
To estimate the variety of vulnerabilities discovered 12 months by 12 months, it’s sufficient to take a look at the CVE (Widespread Vulnerabilities and Exposures) statistics. The graph beneath exhibits the variety of vulnerabilities discovered from 2017 to 2021. The data is offered by Nationwide Vulnerability Database (NVD).
Listed below are 2 information:
- the variety of discovered vulnerabilities will increase yearly;
- the distinction between the variety of vulnerabilities in 2017 and in 2021 is greater than 30%.
By the way in which, on the time of writing the article in 2022, greater than 5 thousand vulnerabilities have already been discovered.
Needless to say vulnerabilities can exist for years earlier than they change into publicly recognized. Take at the very least the sensational Log4Shell (CVE-2021-44228), that was disclosed 8 years after its look. Attackers can exploit a hidden vulnerability till it’s found — in consequence, the enterprise is dropping cash.
What should be accomplished? Use complicated approaches and instruments that may mean you can detect as many safety defects as potential.
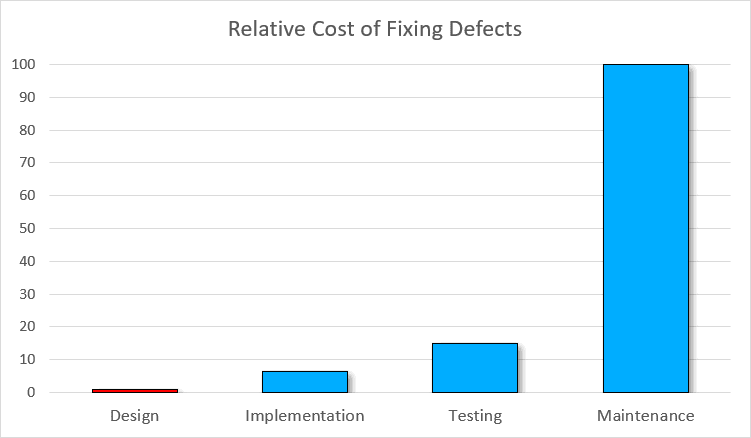
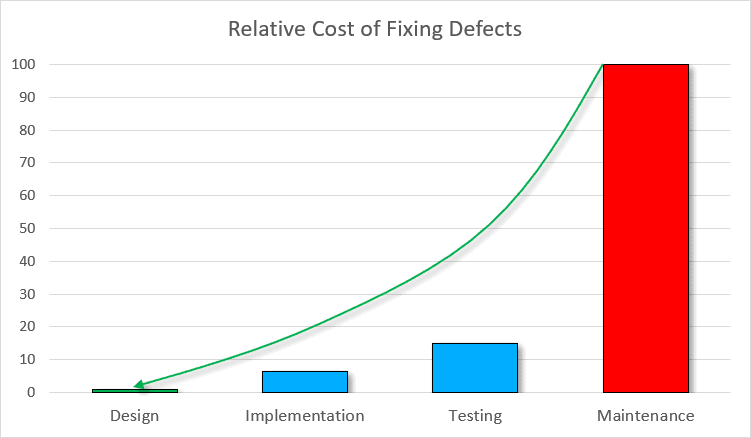
Reality #2: vulnerabilities discovered later are costlier to repair
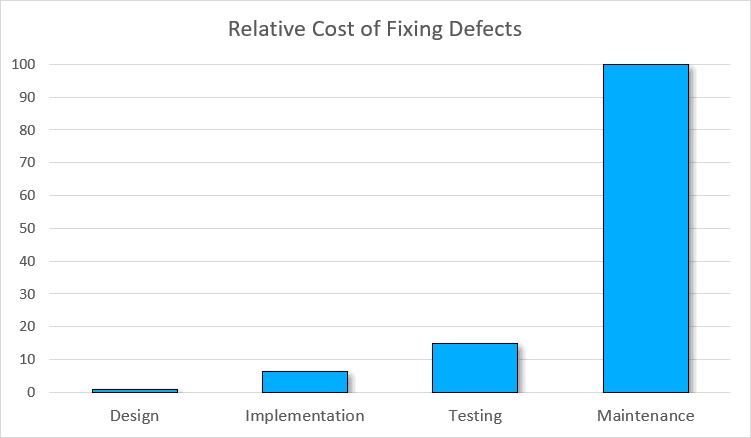
Here is what IBM System Science Institute reports concerning the relative value of fixing the vulnerability:
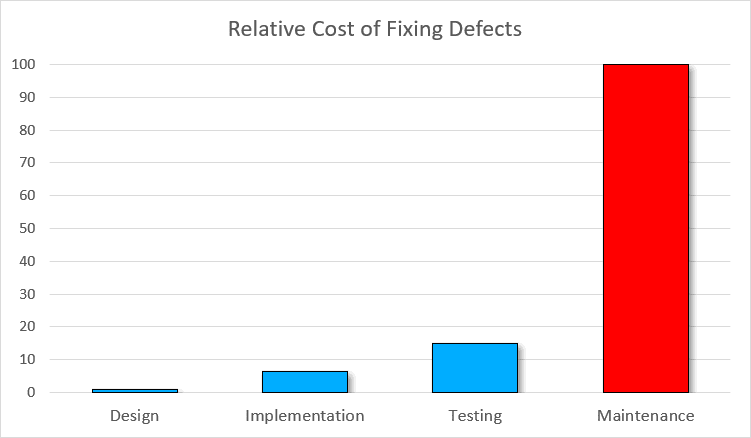
Vulnerabilities discovered after the discharge are 15 instances costlier than these found on the improvement stage. Furthermore, they’re 100 instances costlier than vulnerabilities found on the design stage.
Totally different sources current this graph barely completely different. Nonetheless, the general statistics are the identical: defects discovered later are costlier to repair.
Absolute values rely closely on many components: how essential the vulnerability is, how complicated it’s to patch weak elements, and so forth. Vulnerabilities, as errors, can value hundreds, a whole bunch of hundreds, and even tens of millions of {dollars}. Keep in mind the launch of Ariane 5? The failure losses fluctuate from $360,000,000 to $500,000,000. Or the story of the Polygon Plasma Bridge vulnerability with nearly $850,000,000 in danger.
What should be accomplished? Use instruments and approaches that assist to detect safety defects as early as potential. Let your group enhance their expertise.
3 causes to combine SAST in SSDLC
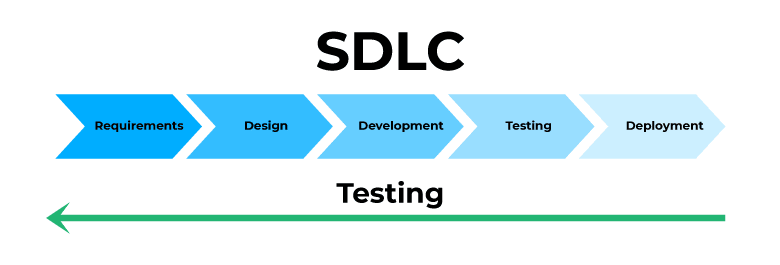
1. Shift-left testing
Shift-left is a observe meant to carry out testing early in software program improvement life cycle. That’s, testing on the timeline of the challenge ought to shift to the left — nearer to the start.
One of many benefits of static evaluation is early defect detection. It is related to SAST as properly. Which means SAST in a DevSecOps pipeline permits you to comply with shift-left testing and detect safety defects earlier to repair them cheaper and simpler.
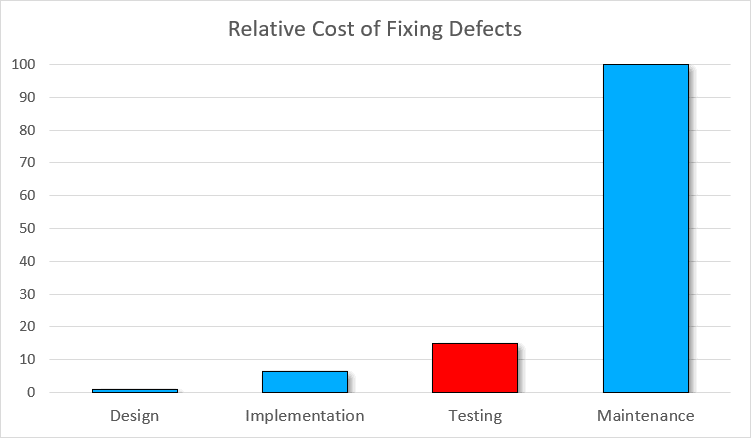
Let’s think about an instance. To estimate the losses, we use the earlier graph that exhibits the relative value of fixing defects. For the standard unit, we take $100.
So, your group is creating an software that works with XML recordsdata. The XML handler is designed as follows:
- the used XML parser processes exterior entities with out restrictions;
- the parser receives the consumer knowledge (taint knowledge) to the enter.
A system designed this manner could also be topic to an XXE assault. Suppose the builders discover out about the issue and repair it on the similar stage. Nonetheless, the losses already quantity to at the very least $100.
Think about {that a} safety defect was not detected and bought into the discharge.
In a worst-case situation, hackers discover the vulnerability and exploit it. The exploitation brings about losses. Nonetheless, neither you nor your shoppers are conscious of this.
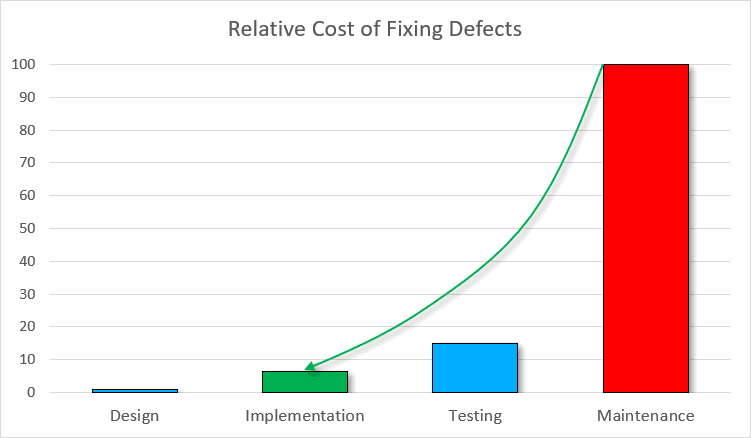
In the end, you can find out concerning the vulnerability. The query is — what reputational injury and monetary losses you and your shoppers have already suffered. Furthermore, you must shut the vulnerability and replace the consumer software program. The graph means that the losses amounted to $10,000. Really, this sounds optimistic.
Suppose an organization makes use of a SAST resolution that may detect this XXE. If SAST is often utilized in CI/CD, builders can discover a safety defect earlier. On this case, clients is not going to get a defective product. And hackers is not going to exploit the safety defect. Consequently, potential losses are considerably lowered. The safety flaw prices about $1,600.
Nonetheless, you’ll be able to handle the method even higher — use a SAST resolution not solely in CI/CD, but additionally regionally — on builders’ machines. This makes it potential to search out the XXE throughout improvement within the IDE. Because the developer is within the job’s context, it is going to be simpler, and due to this fact, cheaper to repair the issue. The safety flaw prices $650.
It seems that SAST in a DevSecOps pipeline helped to chop prices by about 15 instances: from $10,000 to $650. Shift-left testing in motion.
2. Safety defects in exterior code
Typically builders use ready-made options — not solely libraries but additionally code fragments. For instance, code fragments copied from Stack Overflow or from GitHub repositories. The query is — how safe is such code? Alas, there are not any safety ensures.
The “How Reliable is the Crowdsourced Knowledge of Security Implementation?” analysis confirms this. The authors analyzed quite a few questions on Stack Overflow and checked the proposed options for safety. Here is what they discovered:
- 644 out of 1429 inspected reply posts (45%) comprise insecure options;
- on common, reply posts containing insecure options are extra standard and achieve extra feedback and views;
- accepted solutions don’t essentially comprise safe code.
One other analysis — “If you want, I can store the encrypted password” — discusses freelance builders. The paper means that freelancers are much less seemingly to supply safe options if they aren’t explicitly requested about it. Similar to everybody else does, they do not thoughts copying ready-made code, together with code fragments from Stack Overflow.
By the way in which, there may be an attention-grabbing story about copying code from Stack Overflow and the results. We’re speaking about Razer Synapse and Docker for Home windows.
These functions are developed by completely different corporations and appear to be unrelated. Nonetheless, if we run one in all these functions, we won’t run one other. Why?
Builders of each functions used error code from Stack Overflow.
There was an issue with getting a worldwide mutex. Because of the error code, it turned out that each impartial functions used a frequent mutex. You may learn extra about this within the thread on Twitter.
OK, a developer can copy-paste insecure code from Stack Overflow to an software. How can SAST defend the app from vulnerabilities on this case? By analyzing the copied code. SAST resolution can analyze it individually or after its integration into the applying’s code base.
Listen, that typically vulnerabilities seem solely after the mixing of exterior code into the applying. That is why you want to carry out evaluation of the complete software’s code, and never solely the copied one.
3. Enhancing safety expertise of builders
In reality, for those who combine SAST in your improvement course of, you comply with shift-left testing much more exactly. That is achieved by enhancing builders’ expertise within the safety subject.
Earlier we mentioned that SAST shifts the duty for the applying safety in the direction of improvement. This occurs as a result of the builders deal with the warnings of SAST options.
To repair a safety flaw, a developer wants to research the issue. Is it potential to repair SSRF for those who do not perceive what it’s? A path traversal? XEE?
The developer analyses a warning from a SAST resolution and investigates the essence of the safety defect to repair it. The software documentation helps with this. Thus, the developer turns into extra skilled in data safety.
However there may be another essential factor. The developer now is aware of weak spot’ essence. It signifies that they are going to be extra attentive in such instances. Consequently, the chance of getting the same safety defect sooner or later is lowered.
Thus, because the experience will increase, the group will attempt to stop safety defects even earlier than writing the code. This reduces the price of software program improvement.
It’s value noting that SAST resolution builders typically have blogs the place they describe greatest practices of utilizing their instruments, writing safe code and so forth. Such blogs can change into a further alternative for a group to develop new expertise.
Conclusion
Let’s sum it up. SAST permits to cut back monetary and reputational dangers. That is achieved by:
- shift-left testing. Safety defects are detected at an early stage, when their value is minimal;
- evaluation of third-party code. Code copied from Stack Overflow could also be insecure. The identical is with custom-written code. Due to this fact, it’s helpful to examine exterior code for potential vulnerabilities;
- group coaching. To repair the issue discovered by a SAST software, a developer wants to research it. Consequently, the group improves its safety expertise. It helps to stop safety defects even earlier than writing the code.
Regardless of these benefits, you must keep in mind one truth. SAST shouldn’t be a panacea. It is not going to defend you from 100% vulnerabilities, it is not going to repair all points. You may’t create SSDLC solely with the assistance of SAST.
And but SAST is one other important step-up that may assist scale back reputational and monetary dangers. In case you are constructing SSDLC, SAST tools must be a compulsory a part of the DevSecOps pipeline.
And as regular, I invite you to subscribe to my Twitter, for those who do not need to miss new publications.