Exploring JWT, Periods, and Past for Sturdy Internet Safety
Introduction: Understanding Authentication and Authorization
Within the digital world, safety is paramount. For net functions, this begins with a elementary idea: authentication. However what precisely is authentication, and the way does it differ from authorization? Authentication is the method of verifying who somebody is, whereas authorization is the method of verifying what particular functions, information, and information a person has entry to. In net growth, significantly for frontend builders, understanding these ideas isn’t just about enhancing safety but additionally about making certain a seamless person expertise. How do you make sure that the particular person requesting entry to a useful resource is who they declare to be? And as soon as their identification is confirmed, how do you management what they’ll do or see?
Exploring Varied Authentication Strategies
- Fundamental Authentication: It’s the best kind, the place person credentials are despatched with every HTTP request. Regardless of its simplicity, it’s much less safe and customarily used for easy, low-security functions.
- Token-Primarily based Authentication: Entails exchanging person credentials for a token, which is then utilized in subsequent requests. It’s safer and appropriate for functions the place classes usually are not sensible.
- OAuth: An open commonplace for entry delegation, generally used for third-party entry, comparable to “Log in with Google”.
- Utilizing Libraries like Passport: Passport.js and comparable libraries provide versatile and modular authentication options for numerous authentication strategies.
JWT vs. Session Authentication – The Fundamental Variations
The talk between JWT (JSON Internet Token) and Session-Primarily based Authentication is a vital level in trendy net growth.
-
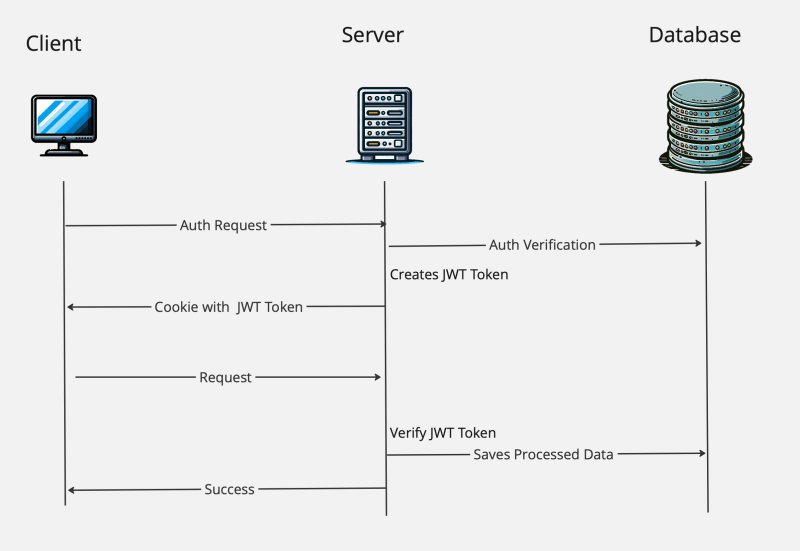
JWT Authentication: Right here, the server generates a token that the consumer shops and presents with every request. It is a stateless technique, that means the server does not have to hold a document of the token.
-
Session-Primarily based Authentication: Contrarily, it is stateful. The server creates a session for the person and shops session information on the server-side. The consumer holds solely a session identifier, usually in a cookie.
What’s JWT?
JSON Internet Token (JWT) serves as a compact and self-contained mechanism for securely transmitting info between events as a JSON object. Essential in frontend growth, JWTs are used not only for authentication but additionally for info change, making understanding their nuances important.
JWT Construction:
- Header: Specifies the token sort (JWT) and the signing algorithm (e.g., HMAC SHA256).
- Payload: Accommodates the claims, that are statements about an entity (person) and extra metadata.
- Signature: Created by encoding the header and payload with a secret, making certain the token’s integrity.
JWT in Motion:
- Upon person authentication, the server generates a JWT.
- This JWT is shipped again to the consumer and saved, usually in native storage or an HTTP-only cookie.
- The consumer contains this token within the HTTP Authorization header for subsequent requests.
- The server validates the token and grants entry if legitimate.
Benefits:
- Scalability: Resulting from their stateless nature, JWTs are perfect for distributed programs.
- Flexibility: They can be utilized throughout completely different domains and functions.
- Safety: When correctly carried out, they supply a safe strategy to deal with person authentication.
Safety Issues:
- Transmission Safety: It is important to transmit JWTs over HTTPS.
- Storage: Retailer JWTs securely to forestall XSS assaults and different vulnerabilities.
Dealing with Token Expiry:
- Implement short-lived JWTs and use refresh tokens for renewing entry with out re-authentication.
Understanding Session-Primarily based Authentication
Session-based authentication, sometimes called cookie-based authentication, is a technique the place the server performs a pivotal position in sustaining person authentication data.
The way it works:
- Consumer Authentication: The person gives credentials, which the server verifies.
- Session Creation: Upon profitable authentication, the server creates a session document with a singular identifier, person identifier, session begin time, expiry, and presumably further context like IP deal with and Consumer Agent. Shops that in Database.
- Cookie Storage: This session identifier is shipped again and saved as a cookie within the person’s browser.
- Session Validation: Every request from the person’s browser contains this cookie, then server validates the session by querying to Database. If legitimate, the request is processed.
Benefits:
- Simplicity and Reliability: The server’s session document acts as a centralized reality supply, making it easy to handle person classes.
- Revocation Effectivity: Entry may be shortly revoked by deleting or invalidating the session document, making certain up-to-date session validity.
Disadvantages:
- Efficiency Points at Scale: The dependency on database interactions for each session validation can introduce latency, significantly for high-traffic functions.
- Latency in Dynamic Environments: In functions with dynamic purchasers, this latency can affect person expertise, making session-based authentication much less best in such situations.
Conclusion: Making the Proper Authentication Selection
Selecting between JWT and session-based authentication relies on your software’s particular wants. If you happen to prioritize statelessness and scalability, JWT is perhaps your go-to. For conventional functions the place fast management over classes is essential, session-based authentication holds the higher hand. Understanding these ideas and their implications is essential to creating safe and environment friendly net functions.